Forum Replies Created
-
AuthorPosts
-
January 10, 2025 at 8:43 am in reply to: Finishing a clean up. Question about license.txt, radio.txt #145053
I am curious how there could be no differences in two files that have different file sizes, it seems like there should be some difference in file contents even if only in the spacing or returns between lines. If that’s all it is then I suppose you could ignore it, but in case it’s more than that I would suggest that it might just be safer for you to fix this file. What version of WordPress did you download to compare the license.txt file?
It sounds like the radio.txt file just has some kind of key or tracking number in it. I can’t tell you what that is used for without more info on what put it there but it can’t be harmful by itself, and it’s always possible that it was put there by a plugin that you are using and that it is needed for some kind of registration or account tracking purposes. You can always rename it or move it to a secure folder somewhere else to see if the file gets regenerated and then try and determine what scripts are responsible for writing that file.
Does it do this every time you start the Complete Scan?
It sounds like a caching issue on your server but I cannot tell for sure with just that one screenshot.
To help your further, I will need the answers to my prior questions and a screenshot of the complete scan results so that I have a better idea of what is going wrong.
Also, there is no need to delete the Quarantine records. That historic information is safely preserved in the database to aid with future scans and to help troubleshoot when any issue is not fully resolved after the first fix (as with your situation, the more info we save the more data we have to put together a clear picture of what is happening on your server).
The nonce tokens are stored in your database, so if it’s not just the fact that too much time is going by and the tokens are not truly just expiring, then perhaps there is an issue with your WP_options table. Maybe the table is read only or some other process is preventing the nonce tokens from being stored or is removing them from the database.
How long does the scan take and how long after the scan is done are you running the automatic fix on the threats that are found?
Have you tried the quick scan?
Have you tried limiting the complete scan to only the areas where you know that threats are found?
Have you tried fixing some of the threats as soon as they are found without waiting for the complete scan to finish?
Can you send me a screenshot of the complete scan results so that I have a better idea of how long the scan is taking and how many files it’s finding and where they are?
If you click on the other button, to just show the unloaded results, does it give you any error messages that might indicate what is causing this problem?
I’ll need some more info to be able to help you further, as this is not a common issue, and so far there is no evidence provided that would give me any clues as to why this is happening. Could you cat a copy of the error_log file on your server? This might have the information we need to find the cause and fix this issue. You can send the log file and/or any other sensitive data directly to my email address, rather than posting it on this public forum.
eli AT gotmls DOT net
The same malicious code that injected that user into your database is probably tied into the WordPress core to prevent you from using WordPress to delete that user. You should just remove that user record directly from the wp_users table using PhpMyAdmin or whatever database tools are available in your hosting control panel.
This is caused by a new malware infection that is blocking any form that posts array values, so the array of check boxes under “What to look for” on the Anti-Malware setting page is being rejected by the malicious code that has been injected into you website. As a workaround you can click the little red circle button with an “X” in it to delete those options from that form so that the form can be posted…
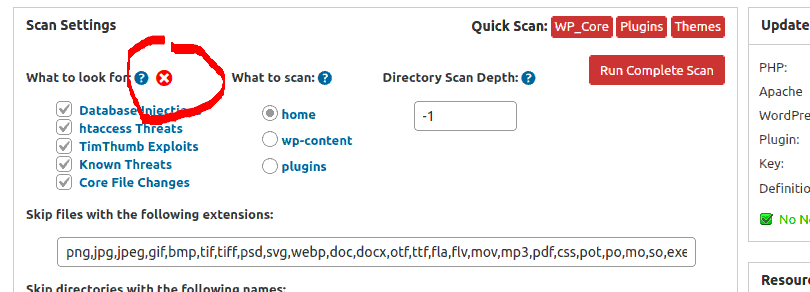
When using the Automatic Fix button to remove this threat from the infected files on your website you may also need to click on the “Go back and try again” button if it fails to fix the selected files on the first try. When you click the Automatic Fix button after that it will attempt to submit the array of threat using a the GET method instead of the POST method, and this should work as long as there are not too many files for your browser to include in the new target URL. If you get an error about the content or URL being too long then try fixing fewer infected files at a time.
Please let me know how this workaround works for you and definitely let me know if you need more help with this.
I agree that those files do not look like WordPress core files, but I would causation you against deleting them if you don’t know what they do or how they are tied into your WordPress install. If any of those files are included anywhere or if the functions or classes defined in them are used in any other included files then just deleting them may cause a fatal error on your website. It would be better to figure out why there is a Read error when my plugin scans them and fix that so that they can be fixed automatically.
If you hover over the file names in that list of errors, does it say why they were not able to be scanned?
Also, are there any error logged in the error_log files on your server that might explain why these files could not be scanned?
If it’s a memory error then try increasing the memory_limit value in the php.ini file on your server?
You can also try downloading these files via FTP and sending them to me so that I can check them myself (but the scan error might have more to do with your server or website configuration then anything to do with the files themselves).
Please let me know if there is any other way I can help you figure this out.
My plugin does not stop DDoS attacks on WooCommerce. The Brute-Force Login Protection only helps protect from attacks of this kind on your wp-login page. For WooCommerce you will likely need to formulate some kind of custom defense since your WooCommerce store will have it’s own structure and this exploit will be tailored specifically for your store.
Try to find a commonality in your access_log files that you could block with an .htaccess Rule, or else add some additional CAPTCHA to your checkout process with a CAPTCHA plugin that is designed for WooCommerce integration.
There are many reasons why your server might not be able to start a persistent session. To start trouble shooting I would suggest that you check the sessions.save_path in the php.ini file on your server. Then verify that the path specified is writable by your web-server user and make sure that the partition containing that folder is not full or mounted Read-Only.
You may also need to get your hosting provider to check on this if you do not have the proper access to your server.
That 500.php looks like a false positive, there is no Eval or any kind of Request Execution in the code you posted. The redirect behavior on your site must be coming from some other code. Was there nothing else found by your hosting provider?
Can you send me a screenshot of the scan results from my plugin?
You can email me directly with any other details.
Do you have any evidence that your site has actually been hacked besides that alarming message from malcare?
The fact that bots are causing 404 errors in your log files is not surprising, this is pretty much a given on most any website. When bots ask for pages that do not exist on your server the 404 error message is the appropriate response, so this is not something I would be worried about.
I don’t see any reason why you would not be able to download a backup of your website. Even if it is potentially infected with a malicious PHP script downloading these files to your PC would not post a direct threat as they are designed to be executed through a web server and typically will not function on a PC without installing and configuring web server software on your local machine.
If you have any other evidence that your site might actually be infected with a real malicious threat of some kind then please send me a link so that I can check it out for you. Otherwise, I would not be concerned about an alarming yet vague warning from a plugin that will not tell you what it’s found unless you give them money, to me this is just as bad as ransomware when it is likely that they have not actually found any malicious hack on your site.
This sounds like a caching issue. If you clear your cache and refresh the page it should show that you are already registered, or given enough time the cache may expire and this page would then show the correct registration status.
Please let me know if you are still having any issues with this and I can help you troubleshoot further.
If you have moved the site to a new server and it is still getting hacked on regular intervals then you most definitely have a backdoor script or a Zero Day vulnerability on the site that is letting in this hacker.
You can find the script responsible by reviewing the access_log files on your server. You just need to look at what URL was requested at the exact time of the last infection. You can get the infection time on the Anti-Malware Quarantine page. Please note, the quarantine and infection times are stored in GMT/UTC so there may be some conversion required if your server logs are in the local time of the server.
Please let me know what you find or if you need more help. You can email me directly with your log files and a screenshot of your Quarantine if you cannot find the relevant entries. If you do find a new threat that is allowing this hack then please send me that file as well so that I can add it to my definition updates.
September 11, 2024 at 4:24 pm in reply to: Known javascript malware: malware.injection?96.12 #135980I have just been updating my definition database with a lot of new threats today and I think the one you have on your home page was in that batch.
Can you please download the latest definition updates (version O9BGI or later) and run the Complete Scan again to see if this remaining threat is now identified and fixed by my plugin?
Your website is loading fine for me now. Did you already figure out what was wrong?
Please let me know what you did to fix it, or if you are still having trouble please send me a screenshot so that I can see what page you are having an issue with.
-
AuthorPosts

